
Rob Labbe, a Canadian, is the co-founder of the Mining and Metals Information Sharing and Analysis Centre. When addressing the topic of cyber security, Labbe admits, “traditionally, mining (cyber) security hasn’t been seen as a major priority.” The reasoning for this is that he partly suspects "there’s an attitude of ‘nobody’s after us. We have nothing anybody’s interested in.’ That was the prevailing sense of the board room” until Canadian-based mining companies started getting hacked.
Typically, when we think of cyber risks we think of early 2000’s-era low-grade computer viruses causing pop-up ads that were easily solved by installing a McAfee or a Norton Anti-Virus program onto our computer. Times have changed in the past 20 years. A firewall and a security operations centre are no longer enough.
Mining operations have become much more integrated with technology and the internet of things: automated and industrial control systems, life-safety systems, wireless crash-avoidance systems in trucks, environmental control systems, etc.
Labbe further points out that “hackers remotely raised the temperature and destroyed a blast furnace at a German steel mill.” It goes beyond pop-ads localized to a single computer or phishing attacks (those e-mails where you are getting asked to wire money to someone and the grammar is usually off a little).
The Mining Journal’s recap of Telstra’s Cyber Security Report emphasizes this evolution, advancement and integration with technology. “Mining is undergoing the most significant change since the introduction of modern industrial equipment. The convergence of IT and operational technology through industrial automation, the uptake of smart devices for real-time operations management and remote operations and the adoption of cloud-based services is driving significant change, creating a data-driven industry.”
Why Hacktivists Care About You (and Why You Need to Care About Them)
Data whether it be cloud-based, remotely stored, or even securely on-site presents a unique risk exposure and is potentially the most critical element to a mining company’s success.
The exploration phase generates big data sets that the geologists analyze to identify new ore deposit locations. The exploration data is expensive to generate and is key to the company’s future growth and success, which makes this data a lucrative target for cyber espionage campaigns.
Imagine your company has been engaged in mining exploration. You’ve successfully found a valuable mineral deposit. You’ve put together your prospectus. You’ve issued a press release. Tomorrow you begin to raise capital from your investor network. This afternoon you have a meeting to secure equity financing.
Now imagine you receive an e-mail informing you that the past three years of data relating to this specific project cannot be accessed. Hacktavists have penetrated your systems and all your technical data is being held for ransom. In the current scenario, without access to your data, your project basically no longer exists.
“Do we even have coverage for this?” is the most commonly asked question. Does your insurance policy cover ransom attacks? Does your insurance policy have broad enough coverage for the re-creation of data? Can you afford to pay for the ransom or data re-creation if you don’t? What impact will that have on your overall business?
The reality is that these risks are real. Operating in overseas and international jurisdictions accentuates them. Mining Magazine highlights the case of Nautilus Minerals having a $10 million payment to a supplier being intercepted for a project in Papua New Guinea.
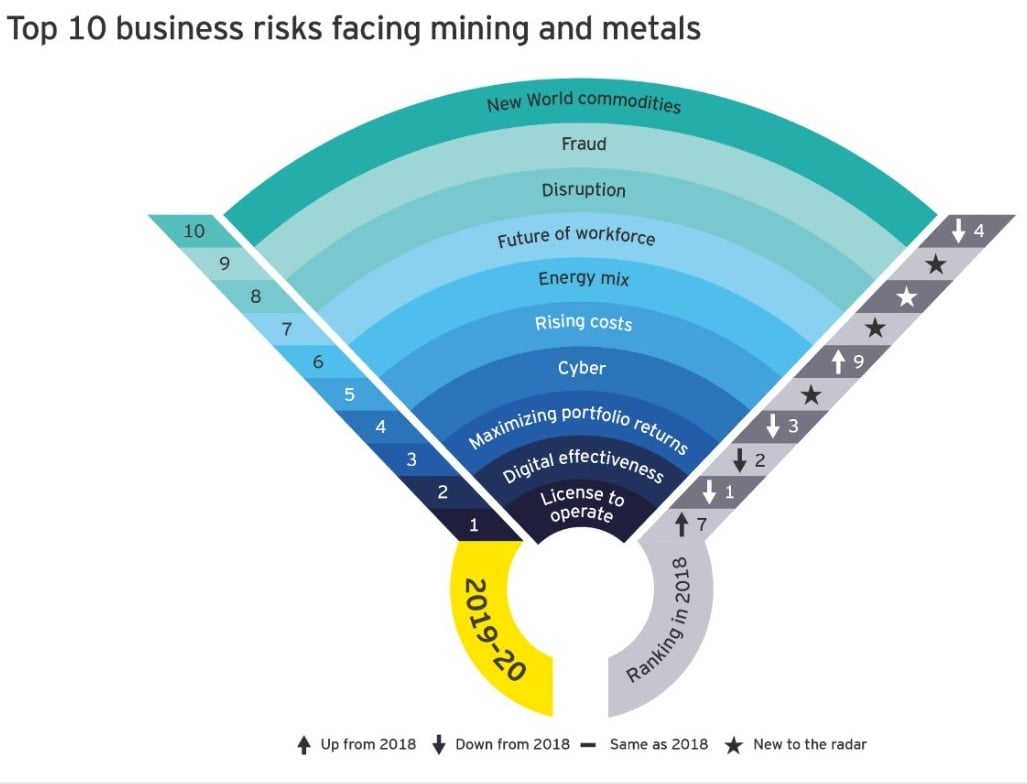
3 Key Principals for Mining Cyber Security Strategy
Ernst & Young sharing the most important risks to mining really drives home the connection between digital systems and cyber security. Cyber security and the digital landscape are about more than just protection. “An innovative cyber security strategy is critical. The focus should be on how cyber security will support and enable enterprise growth. The aim should be to integrate and embed security within business processes and build a more secure working environment for all.
Every cyber security transformation should promote three key principles across culture, governance and capabilities:
- Expect excellence in security fundamentals
- Establish a strong governance program and a culture of accountability
- Build a commitment to continuous improvement
A key element of building a commitment to continuous improvement is having a comprehensive cyber insurance policy. The reality is that most mining exploration and operation companies do not have cyber insurance. Some still hold that view Rob Labbe shares “nobody is after us” or “we have nothing anyone is interested in”. That approach has proven expensive.
The additional reality is that cyber insurance coverage is typically inexpensive, and the cost benefit is overwhelmingly positive. To have your cyber insurance needs properly and professionally evaluated, get your copy of our free Mining & Mineral Exploration Insurance Guide:




